Dear Readers,
This week’s blog is about the Implementation, Best Practices, and Benefits of multi-factor authentication for organizations. Companies are developing or reinvigorating their cybersecurity risk management programs; it’s vital to remember that security threats are a cruel reality. Implementing proper controls to mitigate risks ahead of time is the only way to prevent the harmful effects of such risks successfully.
These numbers only prove that the digital age, with all its advantages, has also introduced greater risks, and both businesses and individuals must go the extra mile to protect themselves.
Due to the pandemic, remote work is rapidly becoming the order of the day and, unfortunately, has become a focus for hackers. That is because, without secure connections set up before going remote, employees’ devices and networks are more susceptible when they are not under the protection of in-office systems.
With this sobering information in mind, you should ensure that your business prioritizes security over convenience when it comes to using MFA and other security measures.
The use of multi-factor authentication is vital, as it ensures that information is only accessed by the intended person, making it harder for cybercriminals to steal. If user data is less tempting, cyber thieves will go for a different one. Multi-factor authentication is a blend of two different factors. One is usually the username and password, which is something the user knows.
Ambimat Electronics, with its experience of over forty years, desires to draw the attention of its readers and potential customers towards this blog post about their new product called AmbiSecure key and how it will benefit us.
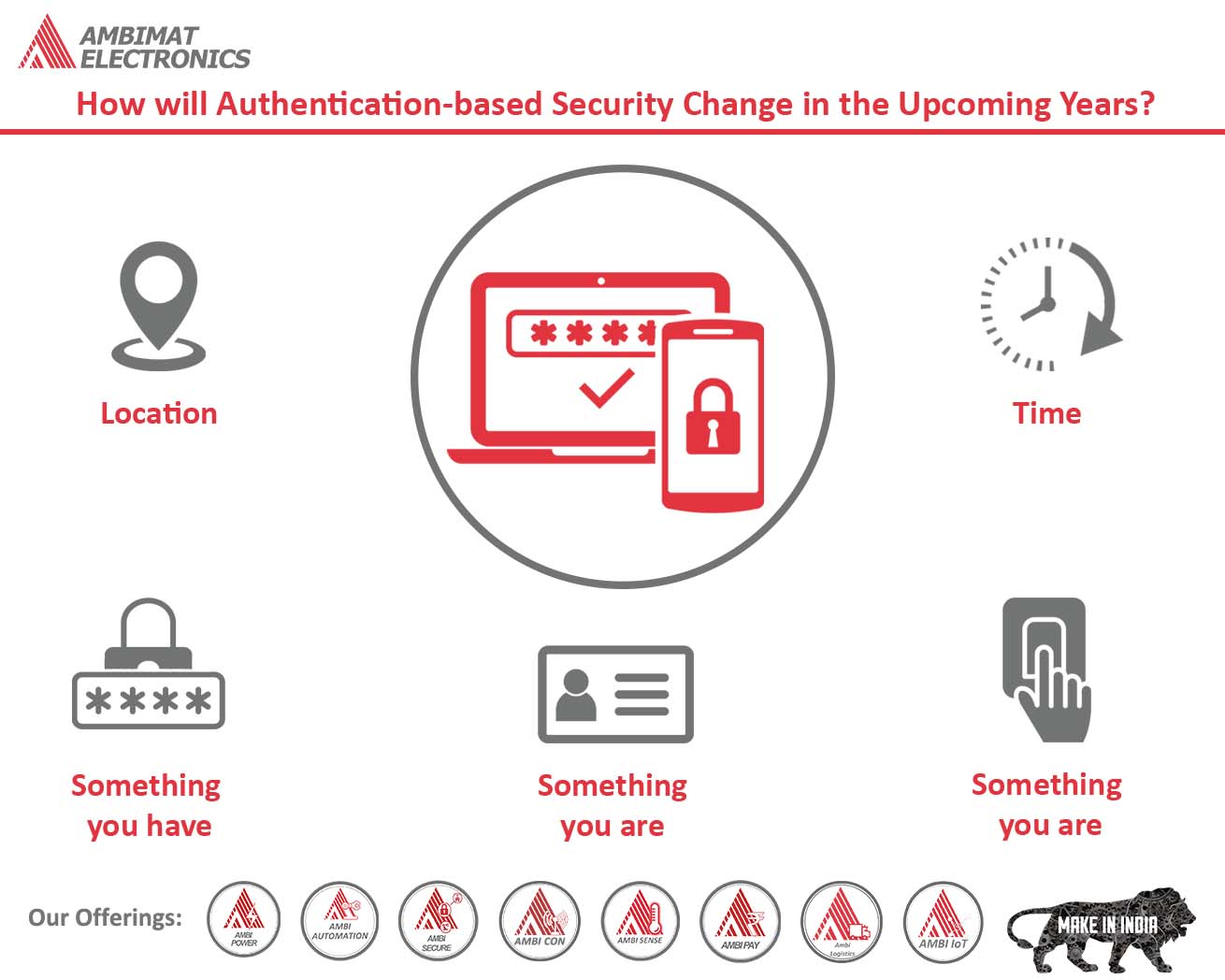
How will Authentication-based Security Change in the Upcoming Years?
Authentication is a crucial element when it comes to data security, yet the transition has been quite slow in embracing modern security and mobility needs. It is becoming clear that simply relying on passwords isn’t enough, and therefore, many organizations are inclining to transform how they can approach authentication. Let us now look into the trends in authentication-based security and the possibility of a passwordless future.
Common Trends
Password-based based authentication has its issues. This is why authentication based on passwords is slowly fading away. According to a Verizon Data Breach Report, 81% of all hacking-associated breaches are either due to stolen or weak passwords.
Passwords are not likely to go away anytime soon. According to Gartner “By 2022 about 60% of global enterprises and about 90% mid-size organizations will implement passwordless authentication systems in more than 50% of use cases.”
Why the use of Password is Declining?
- Inconvenient: Every aspect that revolves around proper password management is considered inconvenient. Users have to remember complex and unique passwords, long passwords are boring, mainly when almost all service requires a password.
- Password Reuse: Due to the inconvenience many users admit reusing their password. Even when users are required to change their password frequently, they make minor changes to it. This practice leads the password to become vulnerable and easy to guess.
- Shared Knowledge: the use of a password requires the password to be stored in a database. Even with passwords being hashed and salted they can be decrypted when a database is breached. If users are guilty of reusing their passwords, then their account is at risk.
Moving from Static to Dynamic Authentication
The COVID-19 pandemic gave way to the remote working environment. Even when it is subsiding, remote working is likely to stay for another couple of years. A survey conducted by Global Workplace Analytics showed that many employees are wanting to continue working from home at least once a week even after the pandemic slows down.
As remote workers become more prevalent and enterprise mobility management becomes more dynamic, adaptive multi-factor authentication (MFA) measures will be required to account for regular changes in device use, location, and login times. In this age of increased mobility, static forms of authentication such as username/password credentials can’t keep up. To maintain authentication-based security in the future, dynamic authentication will need to leverage credentials that cannot be shared or reused.
Minimized Dependence on SMS for Multi-Factor Authentication (MFA)
For quite some time, one-time passwords sent via SMS have been a popular method for multi-factor authentication (MFA). Sadly though, short message services were not designed with security or authentication in mind. Sim cards can be swapped and text messages rerouted to intercept messages sent via cell phones, allowing attackers to bypass this additional layer of security offered by MFA.
Adaptive Multi-Factor Authentication
For a long, multi-factor authentication has been flaunted as a method of improving the security of passwords. Users are required to input additional information over their password, such as OTPs, SMS, or answering a secret question.
Unlike the standard MFA, adaptive MFA further covers security and convenience by demanding more or fewer authentication protocols reliant on the associated risk level of the login session. A user’s risk level for a given session is determined by several factors, including the device used, the time of login, the specific user, and even post-login activities.
Universal Second Factor (U2F), FIDO2, CTAP2, & WebAuthn
U2F has been in development since 2014 but has seen rapid growth since the introduction of the Client to Authenticator Protocol (CTAP) and Web Authentication API (WebAuthn)specs by Fast Identity Online (FIDO2). Passwordless authentication standards aim to overcome the weaknesses found in passwords by combining passwordless first-factor authentication with other authentication measures.
Microsoft describes in their whitepaper on passwordless protection how they’ve worked with FIDO2 to develop enterprise-ready methods of authentication that can replace passwords altogether. In the U2F core, public-key cryptography is based on a hardware key integrated into the device that contains a secret and unique key.
By shifting authentication to include a physical device (rather than simply a password or knowledge-based question) the risk associated with compromised credentials is reduced, as the account cannot be accessed without the physical device.
The FIDO2 authentication method goes beyond what a user knows (passwords, knowledge-based questions, PINs) by utilizing what they have (hardware tokens, biometrics, etc.). It can become more convenient and secure for users to move away from traditional usernames and passwords.
Interesting Facts
Public-key Cryptography: Public-key cryptography stores only the public key in the authentication database. Without the private key, the public key is useless, and the private key is held locally on the device being authenticated, making databases, less appealing targets for attackers.
Single-use keypairs: By using public-key cryptography, key pairs are only associated with a specific source (such as a website) to protect against phishing attacks and man-in-the-middle (MITM) attacks.
Local Credentials: Although PIN-based logins seem to function similarly to passwords, the complexity of the PIN does not ensure security. Since PINs are directly tied to specific physical devices, even if a threat actor knew the PIN, they wouldn’t be able to access the system without direct access to the device. A user can use biometrics to initially log into a device before allowing other authentication factors to gain access to the service.
Conclusion
Enterprises and consumers alike are often slow in adapting new offerings. However, these new authentication-based security options may ultimately replace passwords. Although MFA is steadily rising in the market only a small percentage of people have adopted it as the second layer of protection offered by multi-factor authentication. Even as new authentication comes into the picture, there still be use cases concerning passwords.
Reference:-
https://www.valuewalk.com/2020/06/authentication-based-security-evolution/
Authentication Evolution with AmbiSecure
FIDO2 is a standard that simplifies and secures user authentication. It uses public-key cryptography to protect from phishing attacks and is the only phishing-proof factor available. Corporations around the world and across many sectors, including healthcare, using cloud computing can benefit from Fast Identity Online or Fast ID Online (FIDO) authentication, which their employees and users can use to minimize security risks and improve overall user experience. The AmbiSecure key and card are FIDO certified which offers superior security by combining hardware-based authentication and public key cryptography to effectively defend against phishing attacks and eliminate account takeovers.
AmbiSecure helps organizations accelerate to a password-less future by providing FIDO2 protocol support. Not only does FIDO2 supports two-factor authentication, but also paves the way for eliminating weak password authentication, with strong single-factor (passwordless) hardware-based authentication. The AmbiSecure provides a simple and intuitive authentication experience that users find easy to use, ensuring rapid adoption and organizational security. AmbiSecure key or card does not require a battery or network connectivity, making authentication always accessible.
About Ambimat Electronics:
With design experience of close to 4 decades of excellence, world-class talent, and innovative breakthroughs, Ambimat Electronics is a single-stop solution enabler to Leading PSUs, private sector companies, and start-ups to deliver design capabilities and develop manufacturing capabilities in various industries and markets. AmbiIoT design services have helped develop Smartwatches, Smart homes, Medicals, Robotics, Retail, Pubs and brewery, Security.
Ambimat Electronics has come a long way to become one of India’s leading IoT(Internet of things) product designers and manufacturers today. We present below some of our solutions that can be implemented and parameterized according to specific business needs. AmbiPay, AmbiPower, AmbiCon, AmbiSecure, AmbiSense, AmbiAutomation.
To know more about us or what Ambimat does, we invite you to follow us on LinkedIn or visit our website