Dear Readers,
The blog of this week is about a passwordless authentication system
Through this blog, we aim to make our readers aware of passwordless authentication and how it has the potential to provide convenient access and strengthened security that today’s organizations need to navigate this new environment.
Ambimat Electronics, with its experience of over forty years, desires to draw the attention of its readers and potential customers towards this blog post about their new product called AmbiSecure key and how it will benefit us.
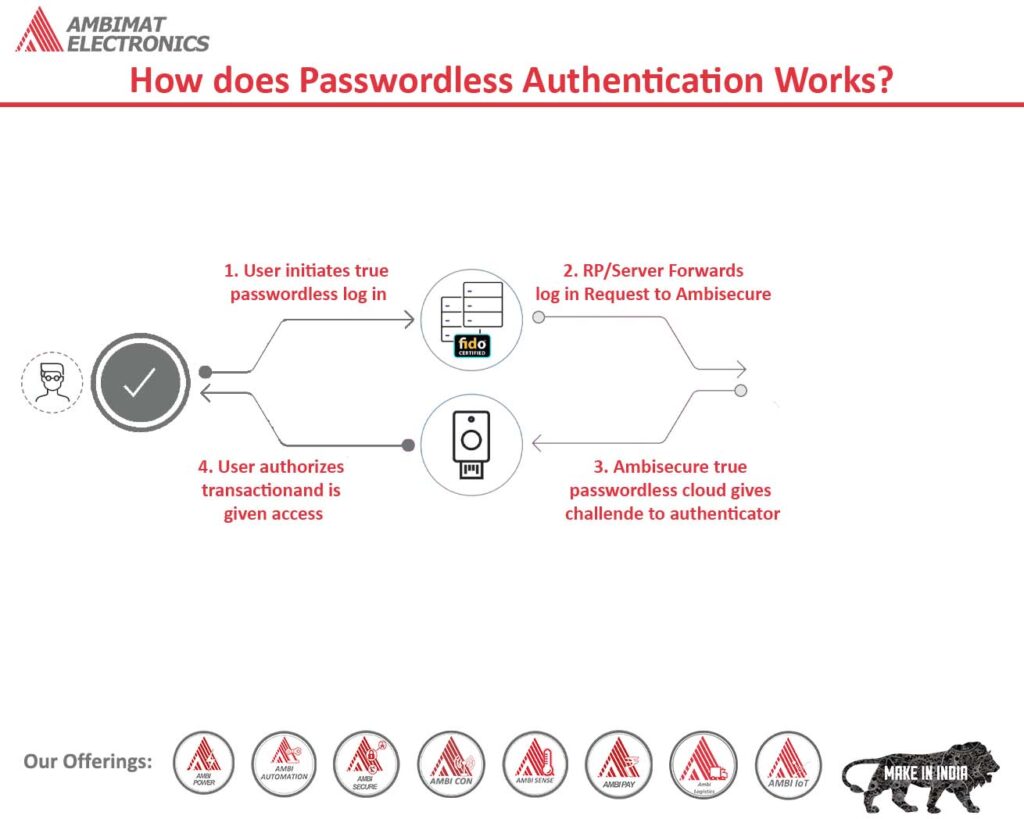
How does Passwordless Authentication Works?
Almost all of us rely on passwords to verify our identity. Unfortunately, there are far from being secure and reliable. Nowadays, traditional authentication such as username and passwords can be guessed easily through brute force attacks. Phishing is another method used by cybercriminals to trick users into revealing their credentials. Another attempt to hack passwords is to install keyloggers that read the user keystrokes on the system.
Even with the knowledge, that legacy passwords are vulnerable; most people still follow poor cybersecurity hygiene like reusing or creating weak passwords for easily remembering them. Such practices make this authentication process useless. This is the sole reason why many organizations are replacing traditional passwords with more secure ways to protect their information. According to Gartner “60% of enterprises worldwide and 90% of mid-sized organizations will employ passwordless methods in 2022.”
What is Passwordless Authentication?
As the name implies, passwordless authentication is the means to verify user identity without the use of passwords. However, what is used are other forms of unique factors for the verification process. These factors can include something the user has (e.g., an OTP received on a mobile device) or something that they are (e.g., biometric such as a fingerprint)
Unlike knowledge-based authentication approaches such as passwords, PINs, or passphrases, passwordless authentication can be more dependable in keeping unauthorized users at bay. This is because passwordless authentication uses factors that are not easily vulnerable to theft.
The Benefits of Passwordless Authentication
Organizations can reduce the risk related to data breaches by implementing passwordless culture. One great benefit of passwordless is that minimizes human error-related problems, such as poor password management. It also strengthens the security of systems that rely on passwords, making them immune to threats, such as man-in-the-middle attacks, credential stuffing, and password spraying.
Going passwordless can also improve efficiency, as it removes the burden of remembering complex passwords and allow users to simply log in to systems without having to enter complicated password combinations. In particular, the IT department can reap the benefits of passwordless, as it lowers IT-related calls due to password resets. This enables them to focus on more important IT tasks.
Organizational operating costs can also be manageable when implementing a passwordless environment. The maintenance and support cost of traditional passwords can be expensive. Work interruption that follows due to password reset can cost organizations massive amounts. According to a survey conducted by HYPR, “57% of employees forget their password and password resets ensues within 90 days.
In short, passwordless authentication provides user verification in a very efficient manner, making the work environment more secure. It also reduces operational costs and work interruptions.
Switch to Passwordless Authentication now
Organizations can implement passwordless authentication in several ways:
- Substitute passwords with unique authentication factorsOrganization should replace legacy passwords with more secure, hard-to-get authentication factors such as fingerprints, voice, facial recognition to verify users. Such factors are hard to duplicate and have been proven to be highly effective at keeping unauthorized users at bay. Many financial institutions have already begun implementing such security features.One-time passwords, hardware security keys, and digital certificates are other widely deployed passwordless authentication methods.
- Enable 2FA passwordless optionsBy implementing two-factor authentication, organization will strengthen its security measures as it provides an additional layer of protection over and above passwords. Although passwords will remain in a 2FA and multi-factor authentication architecture, the majority of 2FA solutions are passwordless by default.For example, most services allow users to access their accounts through the use of 2FA, which requires both password and a one-time PIN. This verification process makes it difficult for unauthorized identities to get past the additional authentication requirement.
There are endless opportunities with passwordless authentication technologies. Relying solely on passwords is considered unwise to secure data and systems. Implementing a strong authentication technology solution will provide a solid cybersecurity infrastructure that addresses organizational needs.
Reference:-
https://www.xbase.com/2021/05/passwordless-authentication-what-is-it-and-how-does-it-work/
Passwordless Authentication with AmbiSecure
FIDO2 is a standard that simplifies and secures user authentication. It uses public-key cryptography to protect from phishing attacks and is the only phishing-proof factor available. Corporations around the world and across many sectors, including healthcare, can benefit from Fast Identity Online or Fast ID Online (FIDO) authentication, which their employees and users can use to minimize security risks and improve overall user experience. The AmbiSecure key and card are FIDO certified which offers superior security by combining hardware-based authentication and public key cryptography to effectively defend against phishing attacks and eliminate account takeovers.
AmbiSecure helps organizations accelerate to a password-less future by providing FIDO2 protocol support. Not only does FIDO2 supports two-factor authentication, but also paves the way for eliminating weak password authentication, with strong single-factor (passwordless) hardware-based authentication. The AmbiSecure provides a simple and intuitive authentication experience that users find easy to use, ensuring rapid adoption and organizational security. Ambisecure key or card does not require a battery or network connectivity, making authentication always accessible.
About Ambimat Electronics:
With design experience of close to 4 decades of excellence, world-class talent, and innovative breakthroughs, Ambimat Electronics is a single-stop solution enabler to Leading PSUs, private sector companies, and start-ups to deliver design capabilities and develop manufacturing capabilities in various industries and markets. AmbiIoT design services have helped develop Smartwatches, Smart homes, Medicals, Robotics, Retail, Pubs and brewery, Security.
Ambimat Electronics has come a long way to become one of India’s leading IoT(Internet of things) product designers and manufacturers today. We present below some of our solutions that can be implemented and parameterized according to specific business needs. AmbiPay, AmbiPower, AmbiCon, AmbiSecure, AmbiSense, AmbiAutomation.
To know more about us or what Ambimat does, we invite you to follow us on LinkedIn or visit our website.