Dear Readers,
This week’s blog is about the Implementation, Best Practices, and Benefits of multi-factor authentication for Protecting Intellectual Property. Cybercrime is an ongoing threat for organizations, with incidents such as ransomware attacks, fraudulent sign-in attempts, and breaches due to stolen credentials continuing to rise. And no organization is safe – cybercriminals target businesses large and small.
Ambimat Electronics, with its experience of over forty years, desires to draw the attention of its readers and potential customers towards this blog post about their new product called AmbiSecure key and how it will benefit us.
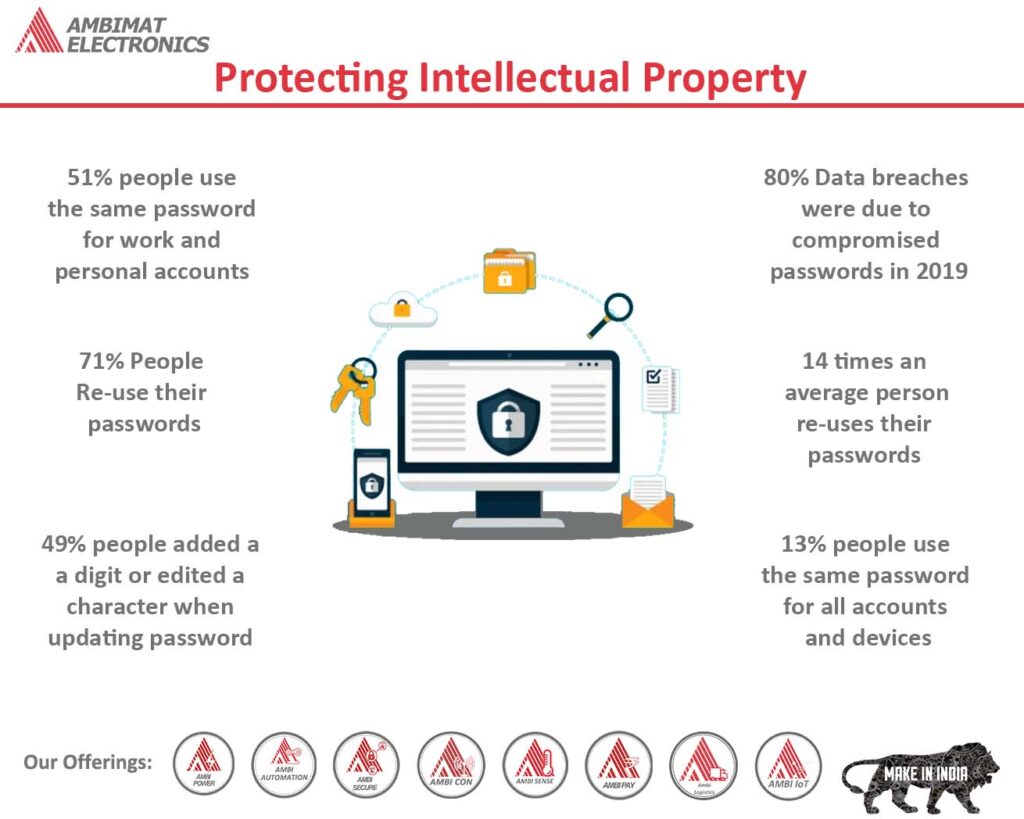
Protecting Intellectual Property
Physical asset of an organization is important, and so is intellectual property (IP). Intellectual property consists of copyrights, trademark, business secret, patent information, and other vital data. It is very crucial to safeguard them, as IP information is linked to several employee know-how and can become vulnerable.
The following are few simple tips that organization can implement to mitigate risk linked to intellectual property theft, and ensure complete safety and security.
Tips to Prevent Intellectual Property Theft
- Set up Information security benchmark and policies
The first and foremost thing enterprise should do to protect IP is to strictly limit access to resources to only users who are authorized to do so, in the organization. Intellectual property data should be need-to-know basis, meaning only the specific department in the organization should have access to it. Access rights should be update periodically to avoid any breaches.
-
- Stay informed about crucial data
Intellectual property relates to all crucial information about the organization and therefore, concerned departments should be fully aware of its whereabouts and who is accessing them. The data related to IP can be copied and saved by employees in their system for ease of working. By ensuring which employee has those files, and how it is being used can reduce data compromise. Employees using IP data should be placed in the high-risk category.
-
- Cybersecurity must be a priority
Organization should adhere to a proper cybersecurity environment to reduces attacks and fight cyberattacks. Senior officials should lay down a strict policy on cybersecurity which all employees must follow, not only in respect to intellectual property, but other data and system as well. A formal training should be conducted from time-to-time for employees to understand the perils of cyber theft and breaches.
-
- Ensure that authorized employee stick to the policy
As time passes many employees start ignoring the security protocols laid down by the organization. Such practice can lead to vulnerabilities. High-risk employees must adhere to the security guidelines, no matter what the circumstances are, to ensure complete safety of intellectual property from being compromised. Organization must enforce a strict adherence policy for authorized employees.
-
- The use of dedicated tool to safeguard IP
There are many dedicated tools to ensure safety of IP information. One of them is the Data Protection tool which helps in loss prevention. Such tools are designed to prevent IP threats and should be implemented as a security feature. It has the ability to know how and where the intellectual property is being used.
-
- Proper Authentication tools
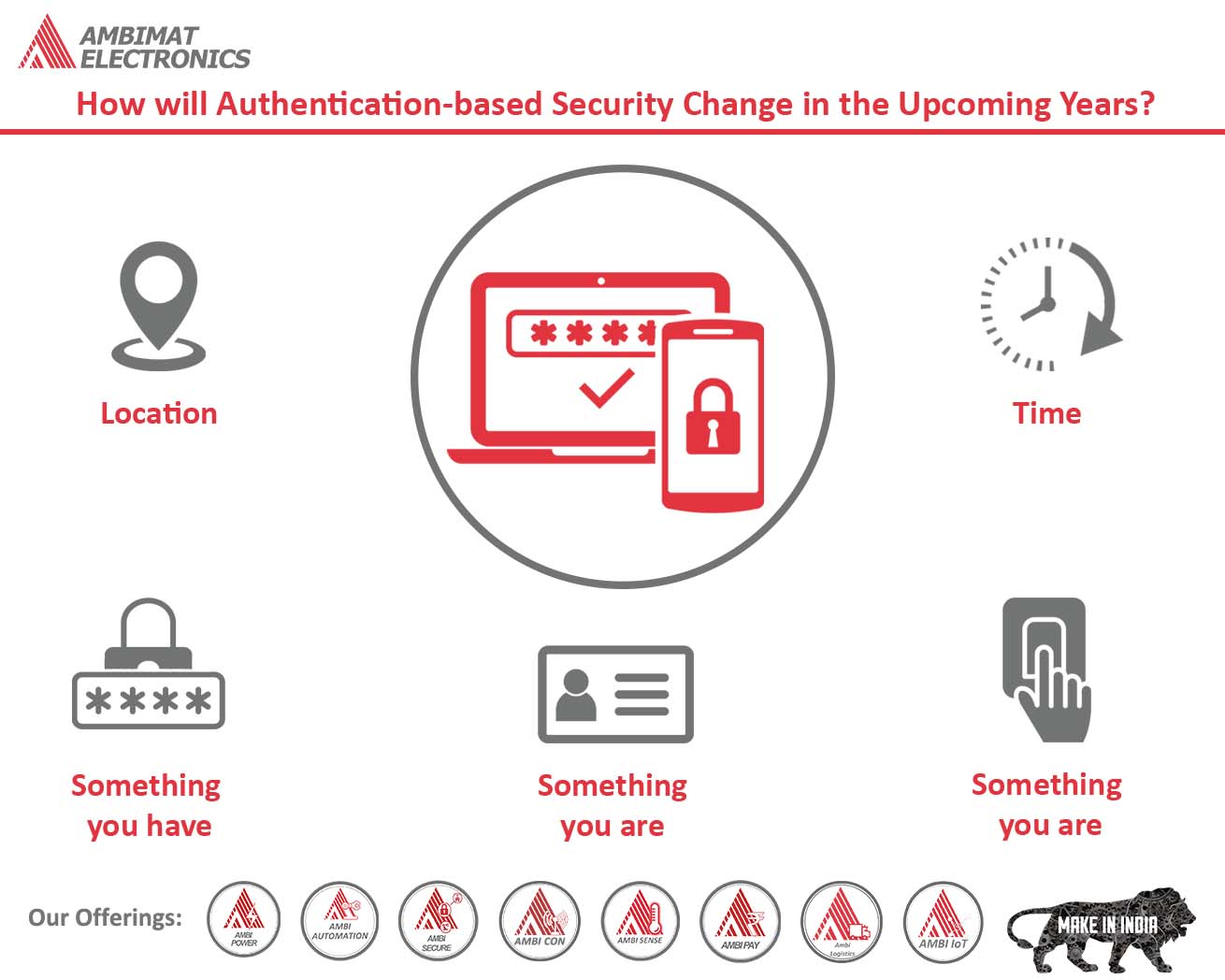
Another method of protecting IP is the use of proper authentication tools. Employees use passwords to protect their system and information in it. However, it is a known fact that passwords can be compromised. Stolen and weak credentials often lead to data breaches. Additionally, the use of complex passwords makes it difficult for employees to remember across multiple devices. To overcome such situation organization can implement two-factor authentication or multi-factor authentication which provides additional layer of security and protects systems and resources. It also provides a seamless user experience.
Although cyber attacks will continue to happen, but following these few tips organization can lay the foundation in preventing their intellectual property from being compromised or stolen.
Reference:
http://Important Security Tips to Prevent Intellectual Property Theft (internetsecurity.tips)
Protect Intellectual Property with AmbiSecure
FIDO2 is a standard that simplifies and secures user authentication. It uses public-key cryptography to protect from phishing attacks and is the only phishing-proof factor available. Organizations around the world and across many sectors can benefit from Fast Identity Online or Fast ID Online (FIDO) authentication, which their employees and users can use to minimize security risks, and improve overall user experience. The AmbiSecure key and card is FIDO certified which offers superior security by combining hardware-based authentication and public key cryptography to effectively defend against phishing attacks and eliminate account takeovers.
AmbiSecure helps organizations accelerate to a password-less future by providing FIDO2 protocol support. Not only does FIDO2 supports two-factor authentication, but also paves the way for eliminating weak password authentication, with strong single-factor (passwordless) hardware-based authentication. The AmbiSecure provides a simple and intuitive authentication experience that users find easy to use, ensuring rapid adoption and organizational security. AmbiSecure key or card does not require a battery or network connectivity, making authentication always accessible.
About Ambimat Electronics:
With design experience of close to 4 decades of excellence, world-class talent, and innovative breakthroughs, Ambimat Electronics is a single-stop solution enabler to Leading PSUs, private sector companies, and start-ups to deliver design capabilities and develop manufacturing capabilities in various industries and markets. AmbiIoT design services have helped develop Smartwatches, Smart homes, Medicals, Robotics, Retail, Pubs and brewery, Security.
Ambimat Electronics has come a long way to become one of India’s leading IoT(Internet of things) product designers and manufacturers today. We present below some of our solutions that can be implemented and parameterized according to specific business needs. AmbiPay, AmbiPower, AmbiCon, AmbiSecure, AmbiSense, AmbiAutomation.
To know more about us or what Ambimat does, we invite you to follow us on LinkedIn or visit our website.