Dear Readers,
This week’s blog is about the passwordless authentication journey.
Passwords require ongoing management from both users and IT staff. For the average user, keeping track of ever-multiplying passwords of varying complexity is, at minimum, a hassle and often a challenge. Forgotten passwords can delay work or trigger account lockouts. Users often reuse passwords across accounts or write them down to aid memory, further compromising an already weak system. Password reuse can also multiply the impact of hijacking, phishing, and data breaches, making it possible for an attacker to unlock multiple accounts with a single stolen password.
Given the security risks and usability problems that passwords present, passwordless authentication is a far better and safer method of ensuring only the right people have access to the right things and for the right reasons.
Ambimat Electronics, with its experience of over forty years, desires to draw the attention of its readers and potential customers towards this blog post about their new product called AmbiSecure key and how it will benefit us.
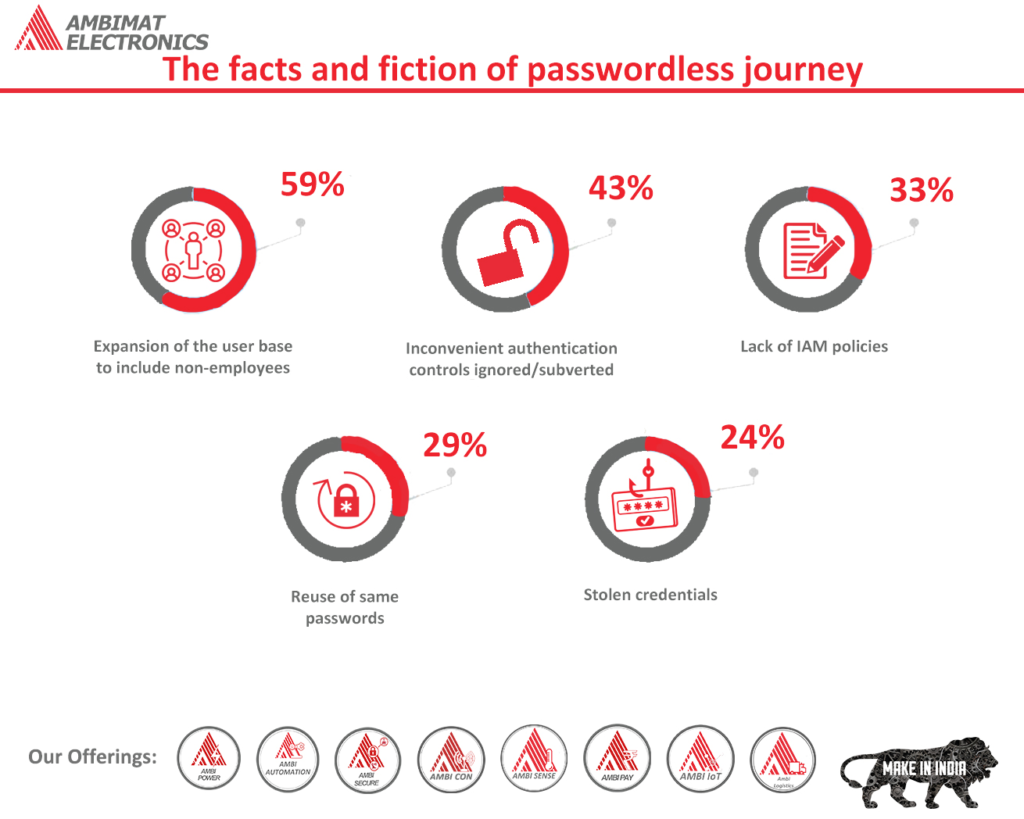
The facts and fiction of passwordless journey
Mentioning the word “passwordless” may have an unpredictable reaction with many security professionals. They may either smirk or simply walk out. Such reaction is understandable as they know that term “passwordless” is a loaded word, and there are many different and contradicting opinions regarding the same.
The objective of this article is to outline the challenges that password displays, the definition of passwordless, and what organizations can look forward to as passwordless authentication develops. Before we begin discussing passwordless, we must first talk about passwords.
The password paradox
The most common form of user authentication is passwords; however, they are not liked by many as they tend to offer poor security and mediocre user experience.
Password is considered a shared secret, as it is known by the user and the validation process is usually stored across several computing devices. Additionally, passwords can be shared over messages or notes. Anyone who knows the secret, including services, or devices can fall victim to cyberattacks.
When it comes to passwords, security and usability are inversely related, this means the better the security the worse the user experience, and vice versa.
So, is it time to say bye-bye to the password? Afraid not.
Even though passwords are vulnerable, they aren’t that bad and are still used for various reasons:
- Convenient and Portable — almost anything can be protected by a password or shared secret — device access, accounts, services, and documents can be protected by passwords. Accessing something becomes very convenient as a password doesn’t depend on anything, hence, making it a simple form of authentication.
- Compatibility — Besides a few exceptions, almost all apps and services use a password. Although some services and apps may require a user to input some additional second-factor authentication for verification, the fact remains that passwords are versatile and universal. The use of passwords has become a daily habit and therefore, we do not have to think twice before concluding whether or not the password is compatible with a particular service.
- Interoperability —Password can easily be given to access computer, smartphone, or anything that we require access to. It is universally supported, and no unnecessary upgrade is required to use them, such as the latest mobile device or installing client software. They simply do their job — to authenticate users.
If the ultimate objective is to abolish password authentication, any substitute must offer substantial improvement in both security and usability without compromising on the above three factors. With keeping this in mind, let us move on to define “passwordless”.
Defining passwordless authentication
Over the years, the word “passwordless” has rapidly grown and today it is being widely used by security, authentication, and identity solution providers — each in its way.
So, to define passwordless we say that “passwordless is the method of authentication where the user does not require a password at login”
Although it seems straightforward, there is a lot to unpack here. There are several implementations of passwordless authentication, and they all have different tradeoffs.
Few passwordless implementations are meant to address usability issues:
Short Message Service (SMS) — As the need to remember is avoided, therefore, many consider that SMS is a form of passwordless verification. Typically, users are sent a one-time
password (OTP) to authenticate themselves. This OTP is effective for a short time. However, OTP is just another form of password.
Email Magic Link — A user receives a unique link in their email and when it is clicked, it verifies the user for that specific device.
SMS can be used as an alternative to send magic links. Nonetheless, both of these authentication flows may provide more usability than passwords, however, both are vulnerable to a phishing attack. Users may be tricked into entering the OTP or clicking the magic link, therefore, both methods of passwordless solution do not offer much security.
Other password implementations are intended to address security issues:
Smart Cards (PIV/CAC) — Smart cards are very efficient in protecting against phishing attacks. The card is inserted into a reader by the user, and the smart card is validated with a unique PIN. This is the perfect method to stop remote phishing attacks in their paths. When it comes to portability, compatibility, and interoperability legacy smart cards are not a good choice. The scalability of traditional smart cards can be costly and complex while implemented. This makes it hard to use and inaccessible for most users and businesses.
Password Vs. PIN
There is not much difference between password and PIN from a usability standpoint — this is something to remember. However, from a security standpoint, they are very much different. When a password is entered, it is validated on a server, unfortunately, this means that it can either be stolen or intercepted. A PIN, on the other hand, is limited to the device. For example, when we use our ATM pin it only unlocks our credit or debit card but is never stored or transmitted elsewhere. This is the reason why when a debit or credit card is stolen, users are only required to set the PIN in the new card.
There are a few reasons why this dissimilarity is significant.
As compared to passwords PINs are more secure
The user still needs to memorize something as most methods of strong passwordless authentication require a PIN.
The PIN is released to perform a function only when user fingerprints or face is read over biometric authenticators, and when biometric isn’t available it reverts to the PIN. So what we mean to say is that PIN is not replaced by biometric authenticators.
Identity platforms and open standards roles
The goal of scalability is achieved through a rich open standards ecosystem that combines security, usability, as well as portability, compatibility, and interoperability. AmbiSecure has supported open security standards from the very beginning, to achieve this goal. It has also made its way by pioneering the Webathon and FIDO open standards to integrate them in operating platforms, and browsers. These standards paired with AmbiSecure allow strong authentication across several devices, applications, and services.
Open standards have also been accepted by identity and access management solutions to deliver the functionality and scalability that organizations require to adopt strong passwordless authentication for business crucial services and applications.
Organizations who have invested in the IAM platform can explore the passwordless option they have to offer. As an alternative to non-Webathon/FIDO passwordless experience, most will have mobile authentication apps to strengthen user experience on various legacy systems. Although mobile authentication apps can be susceptible to phishing, they are considered stronger than passwords which is why IAM platforms support hardware security keys like AmbiSecure.
The bridge to passwordless
This is what the AmbiSecure was designed for — to meet you exactly where you are and to evolve with your security infrastructure. Hardware security keys don’t require client software or peripherals, like card readers. Additionally, hardware security keys are intended to support multiple sets of security protocols. With AmbiSecure phishing resistant hardware security key users can now put a stop to account takeovers as a second-factor authentication above password. Hardware security keys can be deployed in a passwordless environment as a smart card or a FIDO security key in identity and access management scenarios. The AmbiSecure hardware security key is truly a bridge to passwordless.
AmbiSecure for Identity and Access Management Solution
FIDO2 is a standard that simplifies and secures user authentication. It uses public-key cryptography to protect from phishing attacks and is the only phishing-proof factor available. Corporations around the world and across many sectors, including healthcare, can benefit from Fast Identity Online or Fast ID Online (FIDO) authentication, which their employees and users can use to minimize security risks and improve overall user experience. The AmbiSecure key and card are FIDO certified which offers superior security by combining hardware-based authentication and public key cryptography to effectively defend against phishing attacks and eliminate account takeovers.
AmbiSecure helps organizations accelerate to a password-less future by providing FIDO2 protocol support. FIDO2 supports two-factor authentication and paves the way for eliminating weak password authentication, with strong single-factor (passwordless) hardware-based authentication. The AmbiSecure provides a simple and intuitive authentication experience that users find easy to use, ensuring rapid adoption and organizational security. AmbiSecure key or card does not require a battery or network connectivity, making authentication always accessible.
About Ambimat Electronics:
With design experience of close to 4 decades of excellence, world-class talent, and innovative breakthroughs, Ambimat Electronics is a single-stop solution enabler to Leading PSUs, private sector companies, and start-ups to deliver design capabilities and develop manufacturing capabilities in various industries and markets. AmbiIoT design services have helped develop Smartwatches, Smart homes, Medicals, Robotics, Retail, Pubs and brewery, Security.
Ambimat Electronics has come a long way to become one of India’s leading IoT(Internet of things) product designers and manufacturers today. We present below some of our solutions that can be implemented and parameterized according to specific business needs. AmbiPay, AmbiPower, AmbiCon, AmbiSecure, AmbiSense, AmbiAutomation.
To know more about us or what Ambimat does, we invite you to follow us on LinkedIn or visit our website.