Dear Readers,
This week’s blog is about the passwords are seen as a necessary evil. However, they present too many risks to ignore. For starters, passwords are too easy to steal and guess.
Passwords also require ongoing management from both users and IT staff. For the average user, keeping track of ever-multiplying passwords of varying complexity is, at minimum, a hassle and often a challenge. Forgotten passwords can delay work or trigger account lockouts. Users often reuse passwords across accounts or write them down to aid memory, further compromising an already weak system. Password reuse can also multiply the impact of hijacking, phishing, and data breaches, making it possible for an attacker to unlock multiple accounts with a single stolen password.
Given the security risks and usability problems that passwords present, passwordless authentication is a far better and safer method of ensuring only the right people have access to the right things and for the right reasons.
Ambimat Electronics, with its experience of over forty years, desires to draw the attention of its readers and potential customers towards this blog post about their new product called AmbiSecure key and how it will benefit us.
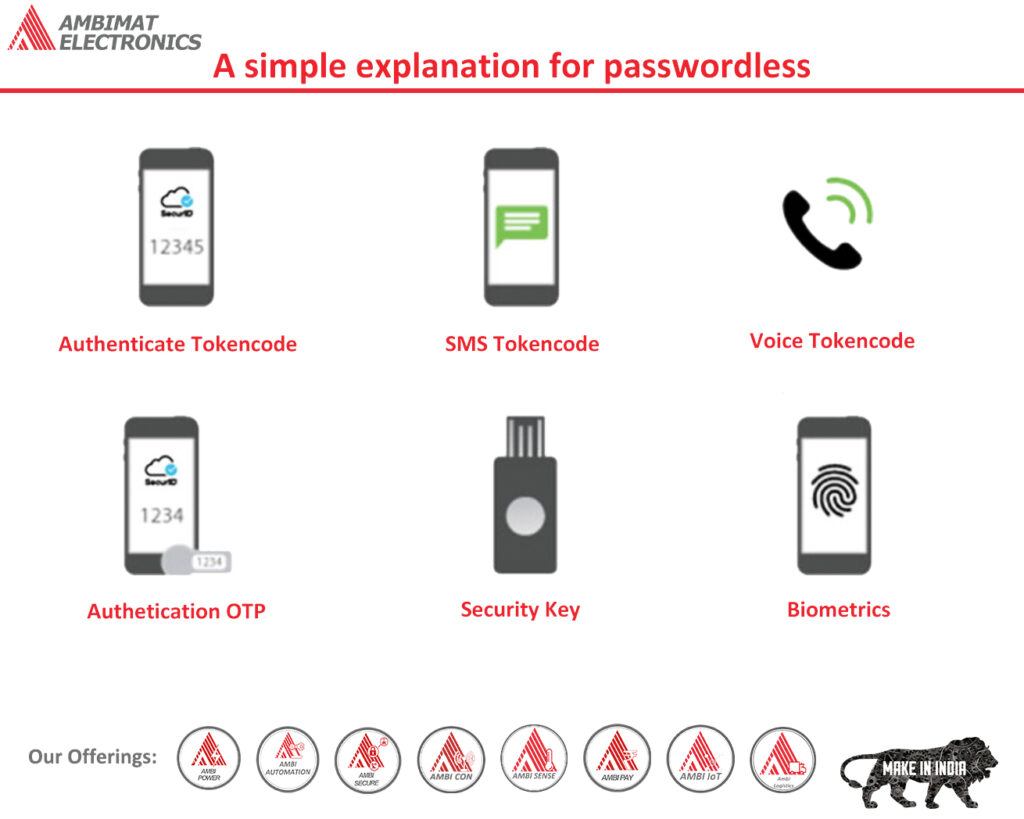
A simple explanation for passwordless
We often talk about passwordless, and of course, some of us may wonder how going passwordless is more secure than having a password? Isn’t it like removing the combination to the safe for the sake of convenience? It is all about asymmetric cryptography, and for those who aren’t familiar with that term, this article is an easy explanation.
The purpose of passwords
Before we move to another alternative to passwords, we need to understand why we have passwords in the first place. Password is meant to identify an individual. They establish that a person is exactly who they claim to be. Unfortunately, there are several reasons why a password cannot be called a unique identifier.
What is Wrong with Passwords?
Passwords are generally stored in a service database. When a user enters their login credentials, it is cross-referenced and verified by the service — hence, the term “symmetric secret” as it shared on both sides. Most users can memorize their passwords while some may use password managers, sticky notes, or other means to remember them. When we hear about breaches and huge password leaks, that is because some malicious person intentionally accessed all the passwords stored within the database. Because of the symmetry, the password being known to both sides and having it stored is the primary reason why passwords are a major security challenge.
Another password issue is that it doesn’t identify you as a person, it identifies what the user knows. Still, a user knowing something doesn’t necessarily mean that it cannot be known to others. For example, a user entering a password can become a victim of shoulder surfing without their knowledge. Anyone can look over a user’s shoulder and get hold of the password they are entering. On the other hand, if a user has something that they own, such as a hardware security key which is hard to replicate by others unless they have it in their possession. So why would anyone put their trust in passwords to protect their most critical and vital information? Password can easily be compromised.
Passwordless Logins
Rather than using a password that is a shared secret or “symmetric secret”, users should switch to “asymmetric secret”. In this method, the secret lies with the user trying to access a service and is never known to the service granting access
Two keys
The asymmetric secret is achieved through the use of two keys — a private key that never leaves the user device (mobile device or computer) and a public key, made available to the service the user wants to access, or log in to.
Despite its name, the public key acts more as a keyhole rather than a key. The public key is unlocked with a digital signature, known as a certificate, created using the user’s private key,
and whether the digital certificate can unlock it or not is determined by the public key. The public key is incapable of viewing the user’s private key, and the private key cannot be replicated or obtained from the public key.
With this method, the user password is never stored in a database for someone to access it. It is only stored locally on the user’s device. There is no way that someone can log in to the application unless they have access to the user’s device and can unlock the same.
Additionally with “asymmetric secret” there is nothing to write down or accidentally reveal the same to others, which would allow them to access an individual account. An asymmetric secret is nothing like a password.
A reliable solution
As an approach to security verification, this method is known by the name of PKI (Public Key Infrastructure) and is nothing new. PKI is used to verify user identity and is a form to replace
passwords. However, the concept has been around for quite something as SSL/TLS certificates for secure online transactions.
A TLS certificate and a PKI validate that the site, a user is visiting, is what it claims to be and is not a fraud. The same technology is applied with the use of hardware security to verify
that a user accessing a service or application is actually who they say they are.
Which is a better identifier?
So, the difference between a password and hardware security is that passwords are required to be stored, or need to be memorized by a user to identify themselves. On the other hand, the hardware security key is stored on a local device belonging to the user and nowhere else. It cannot be removed or viewed by others. Therefore, it can be established that not having a password is safe and secure than having one.
PKI technology from AmbiSecure
FIDO2 is a standard that simplifies and secures user authentication. It uses public-key cryptography to protect from phishing attacks and is the only phishing-proof factor available. Corporations around the world and across many sectors, including healthcare, can benefit from Fast Identity Online or Fast ID Online (FIDO) authentication, which their employees and users can use to minimize security risks and improve overall user experience. The AmbiSecure key and card are FIDO certified which offers superior security by combining hardware-based authentication and public key cryptography to effectively defend against phishing attacks and eliminate account takeovers.
AmbiSecure helps organizations accelerate to a password-less future by providing FIDO2 protocol support. Not only does FIDO2 supports two-factor authentication, but also paves the way for eliminating weak password authentication, with strong single-factor (passwordless) hardware-based authentication. The AmbiSecure provides a simple and intuitive authentication experience that users find easy to use, ensuring rapid adoption and organizational security. Ambisecure key or card does not require a battery or network connectivity, making authentication always accessible.
About Ambimat Electronics:
With design experience of close to 4 decades of excellence, world-class talent, and innovative breakthroughs, Ambimat Electronics is a single-stop solution enabler to Leading PSUs, private sector companies, and start-ups to deliver design capabilities and develop manufacturing capabilities in various industries and markets. AmbiIoT design services have helped develop Smartwatches, Smart homes, Medicals, Robotics, Retail, Pubs and brewery, Security.
Ambimat Electronics has come a long way to become one of India’s leading IoT(Internet of things) product designers and manufacturers today. We present below some of our solutions that can be implemented and parameterized according to specific business needs. AmbiPay, AmbiPower, AmbiCon, AmbiSecure, AmbiSense, AmbiAutomation.
To know more about us or what Ambimat does, we invite you to follow us on LinkedIn or visit our website.
References:-
Reference:-
https://www.beyondidentity.com/blog/tale-two-keys-simple-explanation-passwordless