Dear Readers,
This week’s blog is about how organizations are being forced to move away from passwords. They are specifically asked to justify the costs associated with password support, reevaluating the impact on user experience and, most importantly, justifying whether the password is genuinely doing what it is intended to do – protect the organization from an online attack. Most quickly realize that passwords are antiquated, are a significant cause of frustration, and, ironically, are risk drivers.
Today, organizations are moving towards passwordless authentication, using advanced technologies such as biometric signatures, hardware tokens, cryptographic keys, or PINS to verify users.
The use of multi-factor authentication is vital, as it ensures that information is only accessed by the intended person, making it harder for cybercriminals to steal. If user data is less tempting, cyber thieves will go for a different one. Multi-factor authentication is a blend of two different factors. One is usually the username and password, which is something the user knows.
Ambimat Electronics, with its experience of over forty years, desires to draw the attention of its readers and potential customers towards this blog post about their new product called AmbiSecure key and how it will benefit us.
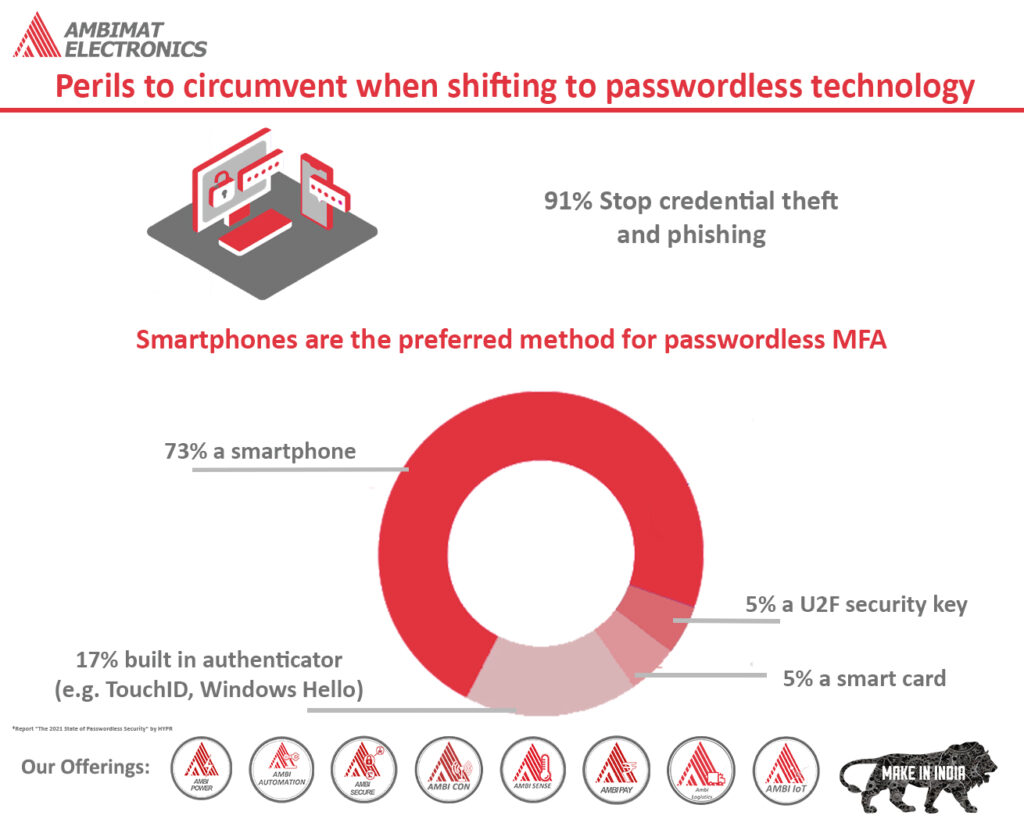
Perils to circumvent when shifting to passwordless technology
The news is filled with reports relating to accounting breaches and password being the main cause of it. However, with the recent trend of passwordless culture, many organizations are considering the advantages of its secure landscape. Apart from being cost-effective, passwordless login provides a streamlined user experience. It also delivers the required security to protect organizations from becoming a victim of cyber-attacks. The remote workforce isn’t slowing down and therefore, organizations must do whatever is necessary to protect remote workers, along with the apps and data that they access to.
The shift to a passwordless journey requires time. However, the final destination is well worth it. Those responsible for the transition should remain vigilant and attentive that streamlined
changeover takes place. Otherwise, the implementation would be inefficient and below standard.
The path to passwordless isn’t similar for every organization. Not everyone would implement the same approach. While others may opt for FIDO2/Webathon passwordless, some may combine both for an effective hybrid approach. Irrespective of the approach they choose, organizations should avoid the common perils that can ensue when shifting to passwordless.
1) Don’t take short-cuts
The legacy methods of implementing security measures should be avoided at all costs when going passwordless. Organizations rushing towards passwordless implementation, without proper testing and planning, should re-assess their execution strategy. Passwordless technology can feature several products which may be implemented at different times as necessary for different levels of users. Regardless of the problems that lie ahead, a company should always be ready and well prepared.
2) Passwordless requires all participants
Going passwordless requires everyone in an organization to participate. It should not be a task solely for the IT department. It brings about a significant upgrade to the organization culture and process, and therefore, requires the involvement of everyone. Solely relying on one department to handle the responsibility will lead to a rough transition and issues for different departments within the organization. When all major players of the organization are involved in passwordless implementation, it ensures maximum user adoption while improving the overall security posture of the company.
3) Don’t skip important implementation due to time limitation
Extreme urgency occurs, especially when responding to a threat or other emergencies. Yet, it is advisable not to skip the initial steps of a project, as they involve chalking out a plan.
On the other hand, the deployment of single or several pilots for the intended users will determine the transition’s readiness before executing it for all users. Let’s now consider a few steps before launching a pilot:
- Confirm the course of passwordless authentication and whether it meets company expectations and works as per the use case.
- A test environment to determine the end-to-end connectivity between the system and authentication technology for users should be set up.
- Organizations should verify that authentication criteria are being met as per their requirement.
4) Don’t overlook the communication factor
Training, testing, and communication is very vital step and shouldn’t be overlooked. Communication is imperative to plan virtual and live events to provide users with in-depth knowledge of solutions and processes for users.
5) Take outside help as and when necessary
When implementing passwordless, it is not necessary that the entire process falls in the hand of the organization. Outside help can be taken to guide the company through the path to passwordless. Selecting outside help with relevant experience will make the transition as effortless as possible, ultimately quickening a company’s journey to passwordless authentication.
Going beyond passwords
FIDO2 is a standard that simplifies and secures user authentication. It uses public-key cryptography to protect from phishing attacks and is the only phishing-proof factor available. Corporations around the world and across many sectors can benefit from Fast Identity Online or Fast ID Online (FIDO) authentication, which their employees and users can use to minimize security risks and improve the user experience. We use FIDO for our AmbiSecure key and card which offers superior security by combining hardware-based authentication and public key cryptography to effectively defend against phishing attacks and eliminate account takeovers.
AmbiSecure helps organizations accelerate to a password-less future by providing support for the FIDO2 protocol. FIDO2 supports not only today’s two-factor authentication but also paves the way for eliminating weak password authentication, with strong single-factor hardware-based authentication. The AmbiSecure provides a simple and intuitive authentication experience that users find easy to use, ensuring rapid adoption and organizational security. Ambisecure key or card does not require a battery or network connectivity, making authentication always accessible.
About Ambimat Electronics:
With design experience of close to 4 decades of excellence, world-class talent, and innovative breakthroughs, Ambimat Electronics is a single-stop solution enabler to Leading PSUs, private sector companies, and start-ups to deliver design capabilities and develop manufacturing capabilities in various industries and markets. AmbiIoT design services have helped develop Smartwatches, Smart homes, Medicals, Robotics, Retail, Pubs and brewery, Security.
Ambimat Electronics has come a long way to become one of India’s leading IoT(Internet of things) product designers and manufacturers today. We present below some of our solutions that can be implemented and parameterized according to specific business needs. AmbiPay, AmbiPower, AmbiCon, AmbiSecure, AmbiSense, AmbiAutomation.
To know more about us or what Ambimat does, we invite you to follow us on LinkedIn or visit our website.