Dear Readers,
This week’s blog is about how cybercrime is an ongoing threat for organizations, with incidents such as ransomware attacks, fraudulent sign-in attempts, and breaches due to stolen credentials continuing to rise. And no organization is safe – cybercriminals target businesses large and small.
The use of multi-factor authentication is vital, as it ensures that information is only accessed by the intended person, making it harder for cybercriminals to steal. If user data is less tempting, cyber thieves will go for a different one. Multi-factor authentication is a blend of two different factors. One is usually the username and password, which is something the user knows.
Ambimat Electronics, with its experience of over forty years, desires to draw the attention of its readers and potential customers towards this blog post about their new product called AmbiSecure key and how it will benefit us.
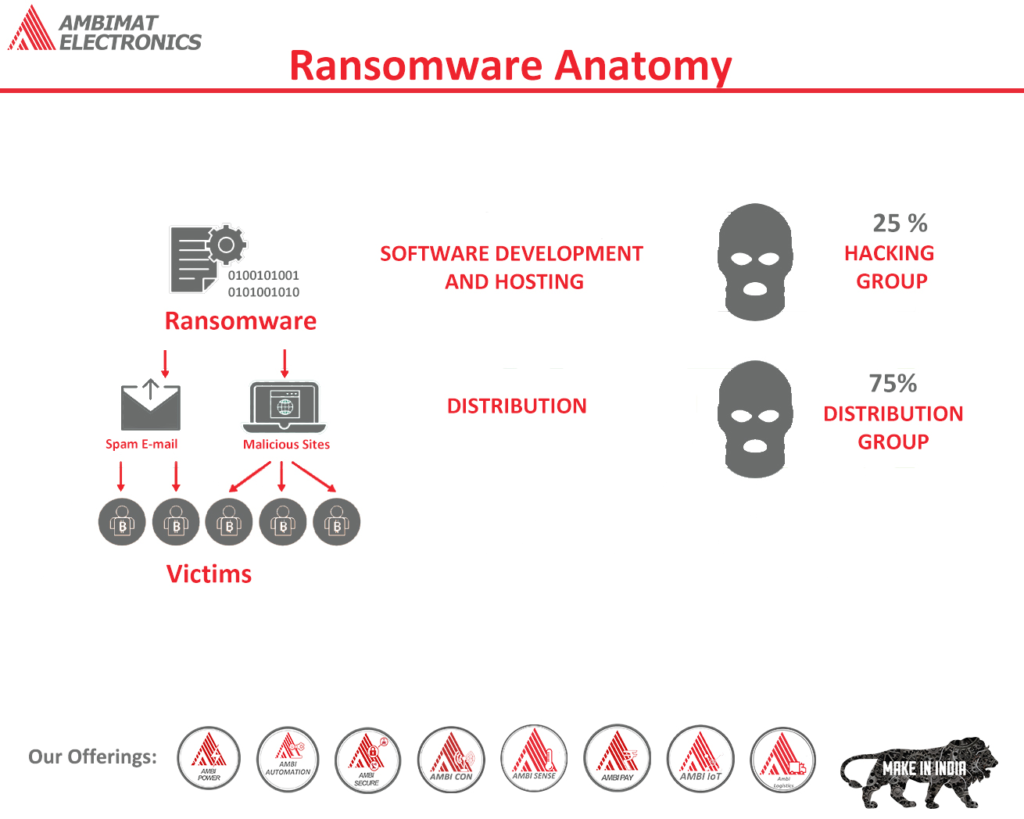
Ransomware Anatomy
It is becoming increasingly common to hear about ransomware in the media because it has been a scourge to enterprises for years. Despite recent headlines involving companies such as Colonial Pipeline and Scripps Health, ransomware has existed for quite some time and has gradually changed over the years. Ransomware has evolved from encrypting individual computers to more recently locking entire organizational files and demanding millions of dollars in ransom payments.
The ransomware industry has become one of the primary interests of criminal enterprises today, and it has developed a “support industry” that takes advantage of this popularity by offering access to large organizations, selling identifications for remote access tools, and laundering cryptocurrency. Cybersecurity threat analysts can monitor discussions, offers, and disputes in crime forums and Telegram groups where ransomware operators frequently participate and mine this data for useful information about how they operate.
Locked and Extorted
Early forms of ransomware typically exploited web browser vulnerabilities to infect the system and install plug-ins, using “exploit kits,” as they are sometimes referred to. Even though exploit kits exist today, their use is less common since the frequency with which new vulnerabilities are disclosed is inadequate to support the effort. Sandboxing and automated patches in browser systems have made exploiting vulnerabilities more difficult.
Victim machines are introduced to ransomware through malware, that surprisingly enough is installed by Microsoft Office documents containing malicious macros. Apart from this, ransomware is also introduced by a third-party manually from a system that has remote desktop protocol (RDP) enabled or through brute force attack. It is particularly easy to find and purchase RDP credentials for servers anywhere in the world for roughly US$10 to US$25 on crime markets like UAS.
Criminals often explore the network and list all available resources, once they have infiltrated the victim’s machine. Sensitive data, if found, it is exfiltrated to a cloud service. Additionally, malware families such as Tricot, Cobalt Strike, various multipurpose tools, and password recovery programs have also been used in many cases. Creating an automation script to distribute the ransomware to as many machines as possible is one of the final steps. The payload, ransom note, and communication instructions are typically pre-configured before the malware is injected into the victim’s network, as many malware families work entirely offline. As a result, enterprises have fewer opportunities to disrupt and prevent.
Recommendations
- Regulate Microsoft Office Macros: Most successful ransomware operations follow a well-known pattern of compromise, which begins with Microsoft Office documents containing macros that entice the recipient to enable content that drops the malicious payload. Additional malware modules are executed once the malicious payload collects the information on the machine and reports it to the command and control domain (C2). The introduction to several malware that leads to ransomware can be prevented by stopping the execution of malicious Office macros. Organizations using the Office suite can stop macros from running which were downloaded from the internet or an email attachment. Leaving the decision of running the macros to the recipient is not the best practice for organizations.
- Use of Multi-factor Authentication: Criminals can get access to a victim system by purchasing information from the dark web, through logs of stealer malware, or by brute force. This usually occurs when the user leaves the system exposed to the internet. Enabling multi-factor authentication is compulsory for remote access tools. Systems can also be configured to limit the IP ranges only for the intended users.
- Backup: Although many users have reported that they do take backup of their vital information, however, the time taken to recover from that backup can be lengthy, hence, they are left with no other choice but to pay the ransom demanded. To avoid paying huge amounts to criminals, organizations should prepare themselves in case of disaster and how to recover from ransomware quickly should be considered.
- Validate Supply Chain: Managed service providers (MSPs) often use cloud management tools. If an account is compromised then ransomware can happen. Multi-factor authentication is required for any service or system that offers persistent access such as this.
- Observe Criminal Marketplaces and Infrastructure: Broker access in criminal marketplaces as well as staging command and control infrastructure is a must for attackers. Observing the threat marketplace can offer insight into what cyber attackers are staging. Moreover, potential breaches can be avoided by the organization that monitors such criminal marketplaces.
- DNS for Visibility & Blocking Command and Control (C2) Communication: Ransomware attacks often involve external communications using the domain name system (DNS) to locate/resolve the C2 destination. A C2 domain is often required for malware to communicate with a threat actor to receive commands. These instructions may include downloading additional malicious tools or exfiltrating data. A valuable source of threat intelligence is DNS traffic. All of this traffic uses DNS. Threat intelligence derived from DNS traffic is underappreciated
and under-utilized by most enterprises.
Prevent Ransomware attacks with AmbiSecure
FIDO2 is a standard that simplifies and secures user authentication. It uses public-key cryptography to protect from phishing attacks and is the only phishing-proof factor available. Corporations around the world and across many sectors, including healthcare, can benefit from Fast Identity Online or Fast ID Online (FIDO) authentication, which their employees and users can use to minimize security risks and improve overall user experience. The AmbiSecure key and card are FIDO certified which offers superior security by combining hardware-based authentication and public key cryptography to effectively defend against phishing attacks and eliminate account takeovers.
AmbiSecure helps organizations accelerate to a password-less future by providing FIDO2 protocol support. Not only does FIDO2 supports two-factor authentication, but also paves the way for eliminating weak password authentication, with strong single-factor (passwordless) hardware-based authentication. The AmbiSecure provides a simple and intuitive authentication experience that users find easy to use, ensuring rapid adoption and organizational security. AmbiSecure key or card does not require a battery or network connectivity, making authentication always accessible.
About Ambimat Electronics:
With design experience of close to 4 decades of excellence, world-class talent, and innovative breakthroughs, Ambimat Electronics is a single-stop solution enabler to Leading PSUs, private sector companies, and start-ups to deliver design capabilities and develop manufacturing capabilities in various industries and markets. AmbiIoT design services have helped develop Smartwatches, Smart homes, Medicals, Robotics, Retail, Pubs and brewery, Security.
Ambimat Electronics has come a long way to become one of India’s leading IoT(Internet of things) product designers and manufacturers today. We present below some of our solutions that can be implemented and parameterized according to specific business needs. AmbiPay, AmbiPower, AmbiCon, AmbiSecure, AmbiSense, AmbiAutomation.
To know more about us or what Ambimat does, we invite you to follow us on LinkedIn or visit our website.