Dear Readers,
The blog of this week is about Improving Security Through Passwordless Authentication.
Through this blog, we aim to make our readers aware of the common two-factor authentication (2FA) techniques and Improving Security Through Passwordless Authentication.
Ambimat Electronics, with its experience of over forty years, desires to draw the attention of its readers and potential customers towards this blog post about their new product called AmbiSecure key and how it will benefit us.
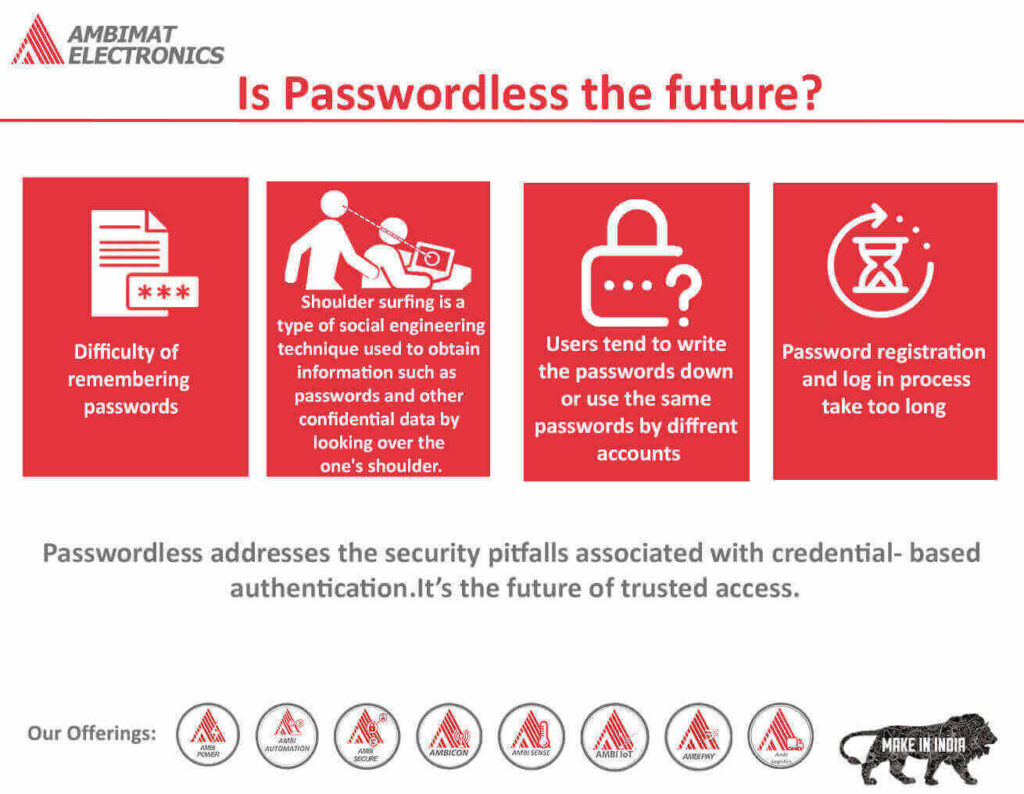
Is Passwordless the future?
Passwords have become an integral part of our lives. Anything and everything, that holds our data requires the use of passwords. Earlier, it seemed easy to remember our credentials but with growing technology, remote work culture, and the growing number of online accounts, it truly has become burdensome to remember every password that we have used or kept, unless we had a computer chip implanted in our brain, but alas we do not. This forgetfulness has led many of us to use low-strength passwords that can be breached easily by hackers. Many organizations have begun to realize this and slowly the world is moving to a passwordless digital culture. However, the importance of passwords remains.
The use of passwords cannot be eliminated because it brings a sense of security to the end-user that their information is safe. However, the approach to passwordless culture, although challenging, cannot be ignored. Many IT professionals believe that the future of their organization now relies upon going from password to passwordless for the end-user.
Passwordless Culture the FIDO Way
FIDO, the fast identity online method provides end-user with a much simpler and risk-free authentication process across many digital devices. So how does it work? Well, FIDO provides strong authentication to the end-user through cryptographic methods, which means that the information is only meant to be used by the person whom it is intended for. These credentials are very unique and never kept on any server. It is solely meant for the user’s device.
Once a user initiates registration protocol on any site. The device which they are using creates a key, both private and public. However, only the public key is registered and authentication can only be proved with ownership of the private key by the user. This is done by unlocking the device being used either by fingerprint scanning, voice input, or any other multifactor verification process. This process helps in removing phishing and the practice of storing weak data credentials.
Process of going from Password to Passwordless
Although the very notion of going from password to passwordless gives a sense of insecurity in many individuals. However, this is not the case and many organizations have now started implementing the same. Lets us now look at the process or the approach of going passwordless.
The first factor of going passwordless is single-factor authentication. This is simply based on pictures or patterns. Studies have shown that many individuals can remember this form of credentials over passwords.
Bio-metric process of authentication. The name says it all. This type of credentials is linked with fingerprints, facial recognition, voice input, and retina identification. Biometric authentication has become a major choice for many companies and is being used in many smartphones and computers as well.
MFA or Multifactor Authentication is often associated with a password in combination with another method verification process. These types of MFA include PIN-protected or SMS-based MFA. Another widely used MFA is the mobile push. This is a form of single-factor passwordless using a PIN or biometric such as fingerprint or voice.
FIDO2 Multifaction Authentication Process
FIDO2 is a standard that simplifies and secures user authentication. It uses public-key cryptography to protect from phishing attacks and is the only phishing-proof factor available. Corporations around the world and across many sectors can benefit from Fast Identity Online or Fast ID Online (FIDO) authentication, which their employees and users can use to minimize security risks and improve the user experience. We use FIDO for our AmbiSecure key and card which offers superior security by combining hardware-based authentication and public key cryptography to effectively defend against phishing attacks and eliminate account takeovers.
Finally, it can be said that although passwords will not disappear overnight. However, the future of passwordless also looks bright. Although it will take time for many to understand its advantages, it will take its shape and place in this ever-growing world of technology.
AmbiSecure helps organizations accelerate to a password-less future by providing support for the FIDO2 protocol. FIDO2 supports not only today’s two-factor authentication but also paves the way for eliminating weak password authentication, with strong single factor hardware-based authentication. The AmbiSecure provides a simple and intuitive authentication experience that users find easy to use, ensuring rapid adoption and organizational security. Ambisecure key or card do not require a battery or network connectivity, making authentication always accessible.
About Ambimat Electronics:
With design experience of close to 4 decades of excellence, world-class talent, and innovative breakthroughs, Ambimat Electronics is a single-stop solution enabler to Leading PSUs, private sector companies, and start-ups to deliver design capabilities and develop manufacturing capabilities in various industries and markets. AmbiIoT design services have helped develop Smartwatches, Smart homes, Medicals, Robotics, Retail, Pubs and brewery, Security.
Ambimat Electronics has come a long way to become one of India’s leading IoT(Internet of things) product designers and manufacturers today. We present below some of our solutions that can be implemented and parameterized according to specific business needs. AmbiPay, AmbiPower, AmbiCon, AmbiSecure, AmbiSense, AmbiAutomation.
To know more about us or what Ambimat does, we invite you to follow us on LinkedIn or visit our website.
References:
https://uat.citi.com/commercialbank/insights/assets/docs/Creating_Strong_Passwords_final.pdf
https://www.cio.com/article/3598532/why-the-future-is-passwordless.html