Authorize.Net mPOS Mobile Application/VPOS v2 Application – Tested Devices
Post on: May 16, 2023
Dear Readers, Below is a list of devices that Authorize.Net has tested and confirmed works with our mPOS Mobile Application/VPOS
Read MoreAppleVAS – About Pass Files
Post on: May 16, 2023
Dear Reader, Passes are a digital representation of information that might otherwise be printed on small pieces of paper or
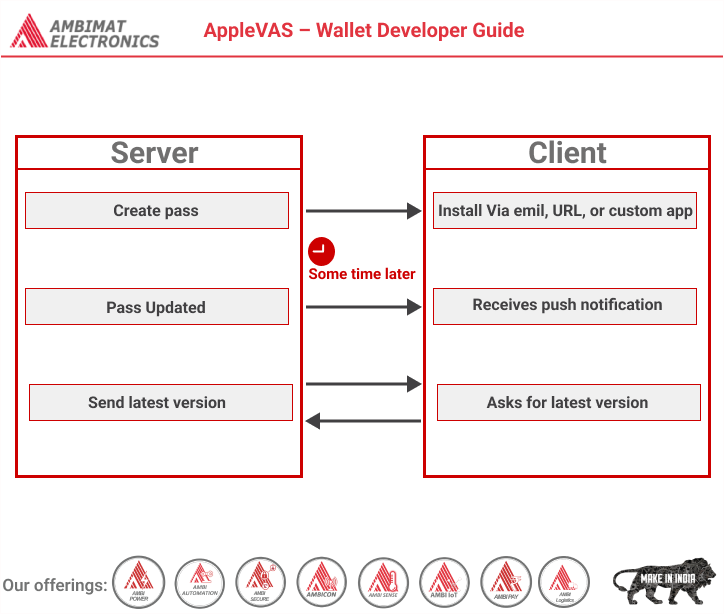
Read MoreAppleVAS – Wallet Developer Guide
Post on: May 16, 2023
Dear Readers, Introducing Wallet Passes are a digital representation of information that might otherwise be printed on small pieces of
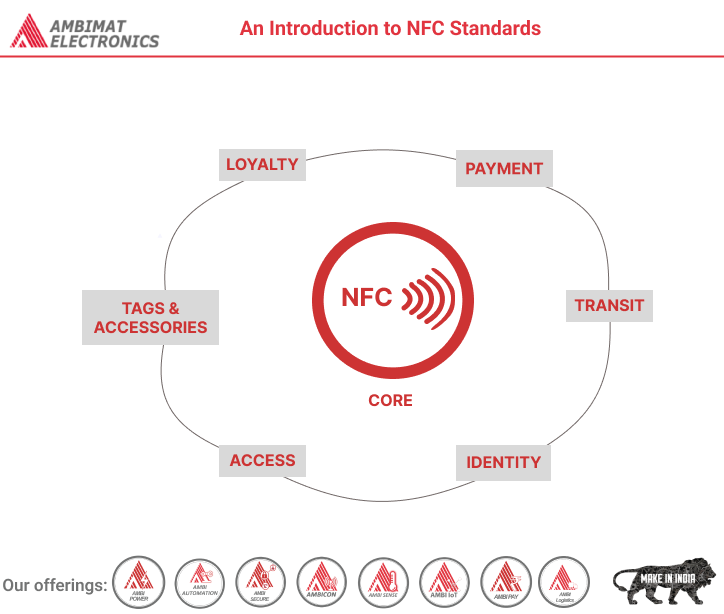
Read MoreAn Introduction to NFC Standards
Post on: May 16, 2023
Dear Reader, We hear a constant buzz these days in the card industry about NFC (Near Field Communications). While it
Read More6″ 3.5 mm Stereo (TRRS) M/F Adapter
Post on: May 16, 2023
Dear Readers, Features Ideal for connecting various swipable card readers Slim design enables the mini-jack to fit through the smaller
Read MoreAn Introduction to MIFARE® Cards | A Beginners Guide From Digital ID
Post on: May 16, 2023
Dear Reader, Are you looking for more information on MIFARE® cards? With so many different options available, it can be
Read MoreEMV(TM) Application Selection
Post on: May 16, 2023
Dear Readers, In order to support the multiapplication business requirement, the terminal should implement appropriate procedures for card application selection.
Read More.jar [File Format]
Post on: May 16, 2023
Dear Readers, A JAR (“Java archive”) file is a package file format typically used to aggregate many Java class files
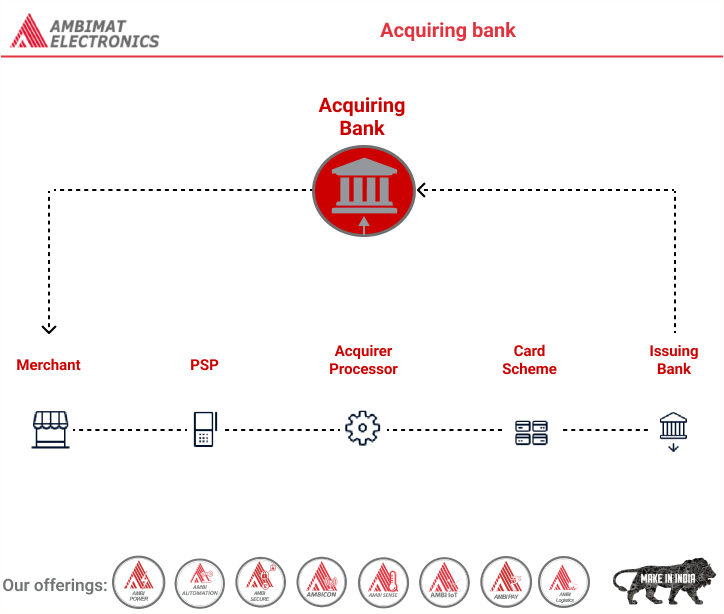
Read MoreAcquiring bank
Post on: May 16, 2023
Dear Reader, An acquiring bank (also known simply as an acquirer) is a bank or financial institution that processes credit
Read More.ipa [File Format]
Post on: May 16, 2023
Dear Reader, An .ipa file is an iOS and iPadOS application archive file which stores an iOS/iPadOS app. Each .ipa
Read More.apk [File Format]
Post on: May 16, 2023
Dear Readers, The Android Package with the file extension apk is the file format used by the Android operating system,
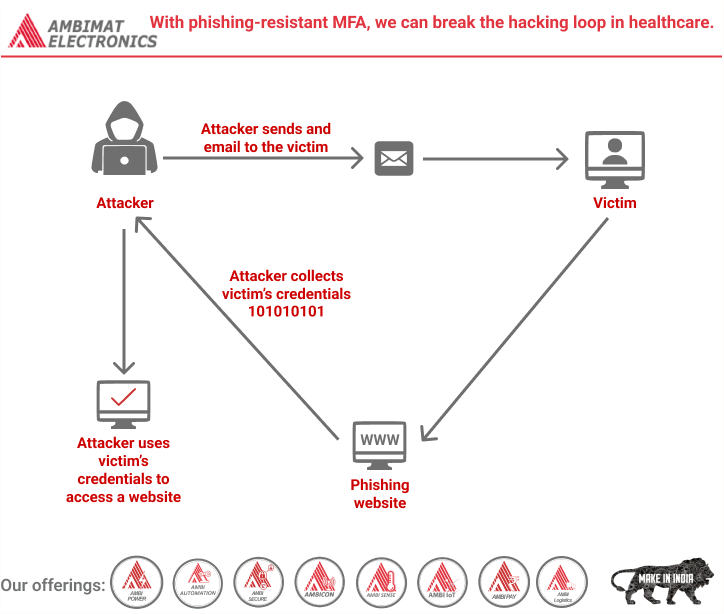
Read MoreWith phishing-resistant MFA, we can break the hacking loop in healthcare.
Post on: May 15, 2023
Dear Readers, Cybercriminals seeking sensitive patient data have increasingly targeted the healthcare sector in recent years. One of the most
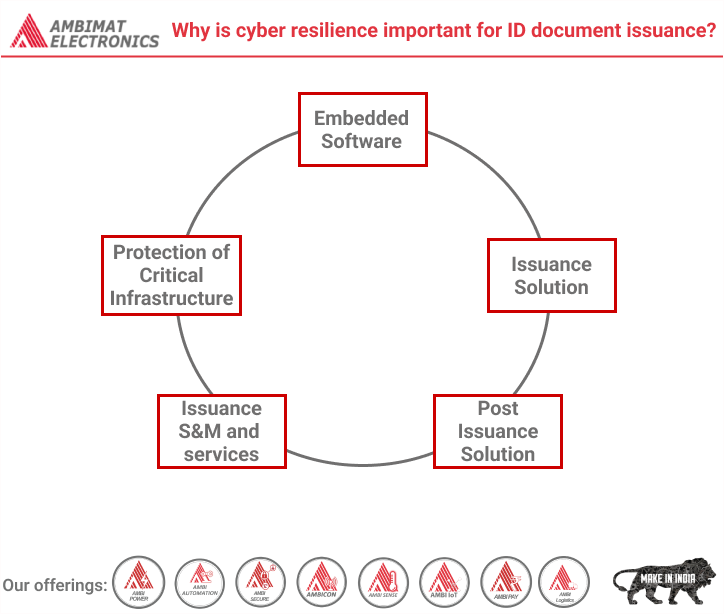
Read MoreWhy is cyber resilience important for ID document issuance?
Post on: May 15, 2023
Dear Readers, To prevent fraud and identity theft in today’s digital era, governments and organizations all over the world are
Read MoreWhy is a password-free future required?
Post on: May 15, 2023
Dear Readers, Passwords have become an integral component of our everyday lives in the digital era. Passwords are used for
Read MoreWhy does the security of passwords still matter in 2022?
Post on: May 15, 2023
Dear Readers, From the inception of the internet, passwords have served as the foundation of online identity protection. Passwords continue
Read MoreWhy AmbiSecure USBKey makes it easier to deploy dependable Cybersecurity?
Post on: May 15, 2023
Dear Readers, Before the invention of hardware security keys, users had very few options for authentication, and none of them
Read MoreWho has the keys in passwordless authentication?
Post on: May 15, 2023
Dear Readers, Users’ usernames and passwords are used throughout the normal authentication process. On the other side, passwords are easy
Read MoreWhat does a hacker look like?
Post on: May 15, 2023
Dear Readers, As the world becomes increasingly reliant on technology, cybersecurity threats are becoming more prevalent. Hackers have evolved from
Read MoreWhat are the benefits of IOT in healthcare, and how can it be secured?
Post on: May 15, 2023
Dear Readers, By enabling medical equipment, wearables, and other connected devices to communicate data to healthcare practitioners in real-time, IoT,
Read More