Dear Readers,
This week’s blog is about Token-based authentication. Token-based authentication allows users to verify their identity and receive a unique access token in return. During the life of the token, users then access the website or app that the token has been issued for, rather than re-enter credentials each time they go back to the same webpage, app, or any resource protected with that same token.
Token-based authentication is different from traditional password-based or server-based authentication techniques. Tokens offer a second layer of security, and administrators have detailed control over each action and transaction.
Ambimat Electronics, with its experience of over forty years, desires to draw the attention of its readers and potential customers towards this blog post about their new product called AmbiSecure key and how it will benefit us.
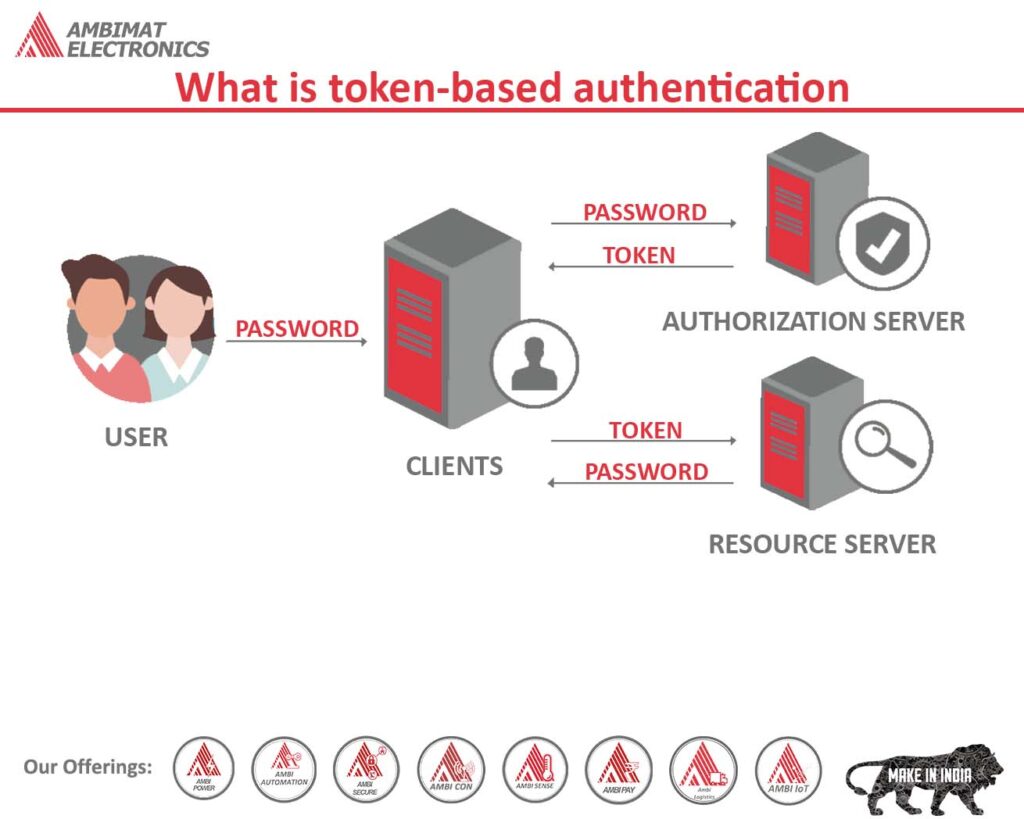
What is token-based authentication?
The proliferation of cloud-based platforms and apps has raised the issue of secure access to sensitive data and resources. Static passwords are no longer sufficient for protecting user access to vital and sensitive information.
With passwords being the root cause of breaches, investing in a new authentication mechanism is time. Employee access cards have replaced the traditional physical keys, and access is granted only when their identity has been validated and their access permission determined. By using token-based authentication, services and resources can be accessed once the requestor has been authenticated.
Defining token-based authentication
Many methods have been developed to mitigate the risks and vulnerabilities associated with password-based authentication. Each authentication method falls under one of three categories: something you know (knowledge), something you are (inheritance), and something you own (possession).
The knowledge factor consists of passwords that users rely on to verify their identities while authentication based on biometrics, such as fingerprints falls under “something you are”. Finally, token-based authentication falls under “something you own”, which is the possession category.
Users need to acquire computer-generated code, referred to as a token before they are permitted to access networks or resources. Token-based authentication is a part of two-factor authentication (2FA) that works in conjunction with passwords.
How does it function?
The token comes in two forms; hardware and software. Despite their forms, tokens are deployed to verify requests to a network or server, just like passwords, but with a more streamlined user experience. Users are no longer required to remember their passwords. With more amount of applications and services requiring user authentication, remembering a login id with a password leads to password fatigue.
Physical (hardware) tokens are usually inserted into a USB port. The system then compares the information provided by the token with the details in its database, and if it matches, the user is authorized to access the system.
Now a days web applications, typically use JSON web software tokens (JWTs) to authenticate their users. JWTs are defined as JSON objects and function within a secure standard for transferring information between parties. An identity provider encrypts user data into a JWT, which is then stored by the service provider, which confirms the user’s identity in each and every request. This prevents criminals from accessing user data held by the identity provider in the event of a breach to the service provider.
Even though these traditional token authentication systems remain in place today, the advent of smartphones has made token-based authentication easier than ever before, transforming smartphones into mobile-as-token authentication mechanisms. Mobile devices, such as smartphones serve as code generators, providing end-users with the necessary security tokens to gain access to the network at any given time. Users must input a cryptographically secure one-time password (OTP token), which lasts about 30 or 60 seconds, depending on the server settings. Such OTP is either generated by an authenticator app on the device or sent through SMS.
Advantages of token-based authentication
One key benefit of token-based authentication is that it removes user dependence on weak login credentials. It enables companies to take the passwordless approach towards identity and access management (IAM) by providing strong multi-factor authentication, including biometrics, push notification, and more.
Platform-as-a-service (PaaS) and mobile apps particularly benefit from token-based authentication. It streamlines the method of securing access to cloud-based and on-premises applications and allows organizations to dynamically implement digital transformation initiatives by sharing their data securely through APIs with several customers, partners, and suppliers beyond their organizational boundaries.
Tokens have other advantages as follows:
- The token is self-contained and has all of the information necessary to authenticate. This allows for scalability since it eliminates the burden of storing session data on the server.
- The generation of a token is disassociated from token verification allowing users to have the option to handle the signing of tokens on a distinct server, or even through a separate company.
- User can easily specify respective roles and permission within the token payload. Additionally, they can also stipulate resources that users can access, offering a seamless user authentication experience.
How secure is token-based authentication?
Authenticating users with just passwords is no longer considered adequate against hackers breaking into organizations’ networks. Users can become vulnerable to brute force attacks, phishing attacks, dictionary attacks, and many other attack vectors used by pernicious beings.
When used with another authentication system, a token-based system creates an extra barrier for attackers to overcome. They can only be stolen from the generator device ―for example, a USB key or a smartphone — nonetheless, token-based authentication is considered to be highly effective and secure.
Even with added advantages, token-based authentication can be vulnerable to security risks. Since OTPs and SMS are factors of can be susceptible to attacks, such as SIM swapping, and can be intercepted by attackers, therefore, they are not considered a best practice to follow. For this particular reason, it is recommended to use authenticator apps to generate OTP tokens. However, losing smartphones or USB keys poses a danger. If both the token and the password are compromised, attackers can access all user resources and secrets, leaving the organization defenseless to criminals’ malicious intentions.
Best practices for managing tokens
Protecting critical corporate assets from data breaches or security incidents requires a robust and effective authentication strategy. For the strategy to be truly effective, identity and credential protection best practices must be adopted and adhered to. Here are some things to consider when implementing token-based authentication:
- Choose the correct token: To choose the right token-based authentication method, you should consider factors such as user experience, scalability, security, and cost.
- Keep tokens discrete: Tokens should be treated like user credentials. Ensuring that your tokens are secure and fully functional is the backbone of an effective IAM strategy. Stolen or compromised tokens are like Trojan Horses.
- Expiration date should be set: Unless the signing key is changed, or unless the token’s expiration is explicitly specified, a signed token remains valid forever. Organizations should have policies and automated solutions for monitoring credentials and revoking expired tokens to avoid authentication issues.
- Leverage HTTPS connections: It is important to use HTTPS when sending tokens to prevent them from being intercepted. HTTPS connections are protected by encryption and security certifications.
The Bottom-line
Passwords should be avoided as much as possible as they are not adequate in protecting corporate resources. Even as enterprises shift to hybrid environments, passwords cannot prevent them from becoming targets to cyber-attacks. Multi-factor authentication should be considered when opting for passwordless initiatives. Token-based authentication can provide a robust security strategy, and an efficient way to manage identity and access management. However, tokens should also be protected from being compromised like every credential.
Token-based authentication with AmbiSecure
FIDO2 is a standard that simplifies and secures user authentication. It uses public-key cryptography to protect from phishing attacks and is the only phishing-proof factor available. Corporations around the world and across many sectors, including healthcare, can benefit from Fast Identity Online or Fast ID Online (FIDO) authentication, which their employees and users can use to minimize security risks and improve overall user experience. The AmbiSecure key and card are FIDO certified which offers superior security by combining hardware-based authentication and public key cryptography to effectively defend against phishing attacks and eliminate account takeovers.
AmbiSecure helps organizations accelerate to a password-less future by providing FIDO2 protocol support. Not only does FIDO2 supports two-factor authentication, but also paves the way for eliminating weak password authentication, with strong single-factor (passwordless) hardware-based authentication. The AmbiSecure provides a simple and intuitive authentication experience that users find easy to use, ensuring rapid adoption and organizational security. AmbiSecure key or card does not require a battery or network connectivity, making authentication always accessible.